Why Microsoft 365 For Business? Every business needs a lot of efficiencies giving the ability to create, cooperate and connect making everything seamless and effective. Every organization needs a system that will enable them to access their company data from anywhere and on any device. When you configure Microsoft 365, you get Word, Excel, SharePoint, […]
In this blog, we will cover the roles of Templates in Cisco SD-WAN. In the previous blog of Zindagi, we have tried to explain why there is a need to switch from traditional networks to Software-Defined Wide Area Networking (SD-WAN). Before we start with templates, you should have a better understanding of each component (vManage, […]
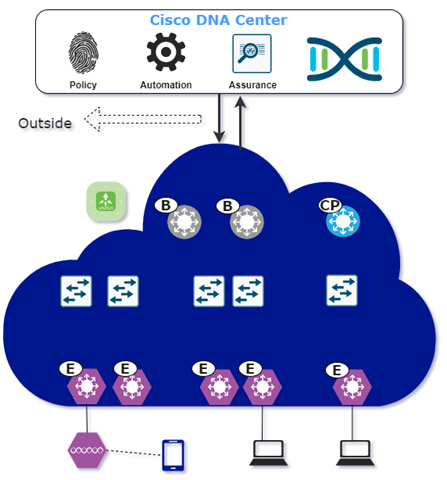
Cisco has released version 2.2.2 of the Cisco DNA Center, which builds on the success of version 2.1.2, which experienced the fastest adoption rate in history. The new Cisco DNA Center has several interesting new features that stay true to the company’s basic mission of providing powerful connections, greater security, and a pleasant IT experience […]
What is Ansible? Ansible Automation Platform has grown over the past years to provide powerful automation solutions that work for operators, administrators, and IT decision-makers across a variety of technology domains. It’s a leading enterprise automation solution from Red Hat®, a thriving open-source community, and the de facto standard technology of IT automation. Installation of […]
How it all started? What is network pivoting? So, after lots of hard work and brainstorming you finally got that sweet Reverse Shell then you escalated your privileges and then you came to know that this current compromised system is not the real target. The TARGET is AD Controller or Admin Desktop and so on […]
Cisco Firepower The Cisco Firepower Next-Generation Firewall (NGFW) is the first threat-focused NGFW in the industry. We can create logical devices like FTD, and ASA on Cisco Firepower. From the network to the endpoint, it provides full, unified policy management of firewall functions, application control, threat prevention, and enhanced malware protection. Perform Initial Chassis Setup […]
In this blog, we will discuss how to install the routing protocols from ASR9K-x64-iosxr-px-k9-7.3.2.tar into the asr9k mini-iOS (asr9k-mini-x64-7.3.2) upgraded version. This installation will help in adding some protocols and features which are not present in the default ASR9K mini IOS XR version. ASR 9006 Router IOS Upgradation & Package Installation Procedure To upgrade IOS […]
As we know today’s Organizations have a big security concern. Signatures are very important to mitigate various types of attacks. Many vendors provide security solutions like NGFW (Next-Generation Firewall), IPS, and IDS. Mostly server-side, and client-side attacks are identified by the signatures. Every Security vendor has an internal Malware Analysis, Incident Response, and Threat Hunting […]
What is an SSRF attack? When a web application fetches a remote resource without validating the URL provided by the user, an SSRF fault occurs. Even when secured by a firewall, VPN, or another sort of network access control list, it permits an attacker to force the program to send a forged request to an […]
In this blog, we will go through the step-by-step process of upgrading the Radware Alteon (Server load balancer) from its old to the new version. What is SLB? A Server load balancer (SLB) is a piece of hardware (or virtual hardware) that distributes network and/or application traffic across many servers by acting as a reverse […]