Procedure To Resolve Your Doubts About WSA User Authentication.
Hello friends! As I already said in my last blog on WSA integration with AD, we will discuss user authentication in this blog.
To create group/user-based policies in WSA or user authentication for Internet access, we need to integrate WSA with AD.
So, before reading this blog, please check out WSA, WSA Policies, and AD integration with WSA.
What is User Authentication in WSA?
Basically, we implement user authentication to confirm that only authorized users can access the internet. It is a way to confirm the identity of a user.
When you enable the authentication, the Cisco WSA authenticates the client by checking the credentials into AD (Active Directory).
We can set up different access policies by user or group using the central user directory. We can also track users using the same.
The only requirement for user authentication is to create an authentication realm. An authentication realm means the integration of WSA with an AD server.
WSA supports 2 different authentication protocols
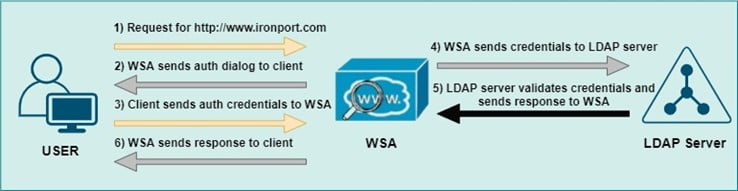
- LDAP (Lightweight Directory Access Protocol) –
- WSA supports both LDAP and LDAPs for authentication.
- Standard LDAP uses version 2 and Secure LDAP user version 3.
- You can define multiple LDAP authentication realms in the WSA.
- LDAP uses a basic authentication scheme.
- LDAP does not support single sign-on
- Passphrase sends in a clear text format.
- NTLM (New Technology LAN Manager) – It is a windows proprietary protocol, supports 2 types of authentication mechanisms.
- Basic –
- When a user tries to open a website then, it asks for a username/password.
- It is supported by all browsers and most applications.
- In this type, WSA authenticates the connection, not the host or an IP address.
- It sends passwords in a plain text format.
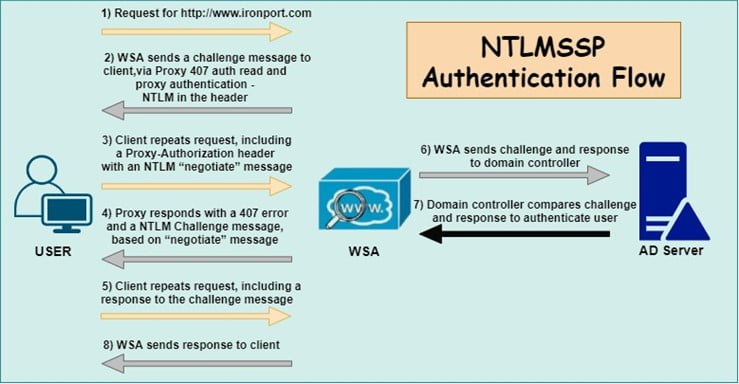
- NTLMSSP –
- The web browser will not ask for the credentials. It uses a 3-way handshake.
- Password doesn’t send to the authentication server; it is more secure.
- In this type, WSA authenticates the connection, not the host or an IP address.
- Basic –
In most organizations, they use an Active Directory server so, they use NTLM. Single Sign-On is also available in NTLM.
Explicit and Transparent Mode Authentication
We can use WSA in Explicit mode or in Transparent mode.
- In explicit mode –
- WSA uses HTTP 407 request and response messages for authentication.
- The user enters username/password and then send It to Web Security Appliance (WSA)
- Then, Web Security Appliance validates the credentials and checks the access is allowed or not for that user.
- In transparent mode –
- WSA uses HTTP 401 request and response messages for authentication.
- The user enters username/password and then send It to Web Security Appliance (WSA)
- Then, Web Security Appliance validates the credentials and checks the access is allowed or not for that user.
User Authentication Configuration
As I already assumed that you have integrated AD with WSA, if not then please check this before moving forward.
Step 1. Identification Policy –
- Login to WSA > Web Security Manager > Identification Profiles under Authentication
- Click on any existing profile or click on “Add Identification Profile” to create new
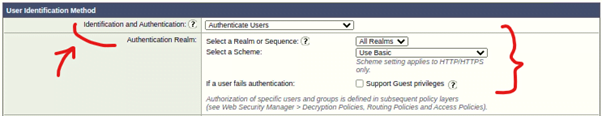
- After AD integration, you will find a new box here “User Identification Method” > Select ‘Authenticate Users’ in the Identification and Authentication dropdown
- Select your Realm (You can choose created Realm) > Select Scheme (In this Scenario, Selecting Basic)
- Click on Submit
Step 2. Access Policy –
- Web Security Manager > Access Policies under Web Policies
- Click on any existing profile or click on “Add Policy” to create new
- Go to Policy Member Definition > You will see new options in the ‘Authorized Users and Groups’ column under the Identification Profiles and Users configuration dialog.
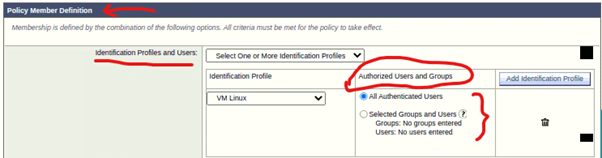
- Here, you can define the users/groups as per your requirement.
- Click Submit > Commit Changes
Note* – If you are configuring from SMA (Security Management Appliance) then you must publish this configuration to the WSA/s also.
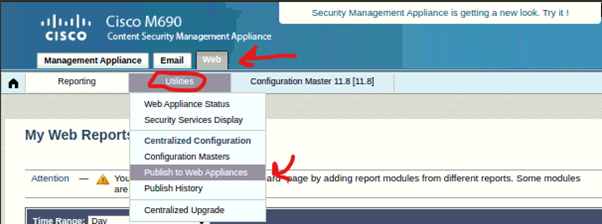
Click on Web > Utilities > Publish to Web Appliances
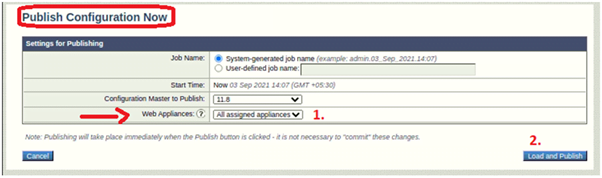
- Click on ‘Publish Configuration Now’ > Select Web Appliances > Click on Load and Publish
In this blog, we checked about user authentication, authentication protocols supported by the WSA, and which is better for your enterprise network. We recommend you use NTLM over LDAP. We hope that we resolve all your doubts about user authentication and different modes of WSA as per authentication.
From this blog, you will implement the WSA user authentication without any hassle but still, if you have any doubts or need any assistance you can contact us directly and we will help you.
Zindagi Technologies has expertise in Networking, Network Security, Data Centre networks, Enterprise networks, Collaboration, Virtualization, etc. We are happy to help you to provide better service for your home and corporate/Enterprise network. You can contact us or give us a call at +91-9773973971.
Author
Jagjeet Singh
Senior Network Security Consultant
