What are the different mechanisms to protect Spanning Tree Protocol (STP)?
In the last blog, we discussed STP and how it works, types of topology change, and their effect on the network. In this, we will explain what different mechanisms are to protect STP.
Types of mechanisms to protect STP are as follows: –
- Root Guard
- Loop Guard
- BPDU Guard
- BPDU Filter
- UDLD
Root Guard
It is a mechanism to protect the root bridge from attack. Attacker connects its switch with lower mac address and priority in the network to become the root bridge, it changes the port role and port state in the topology.
Before the attack on the Root Bridge, communication takes place from PC1 – SW2- SW1-PC2.
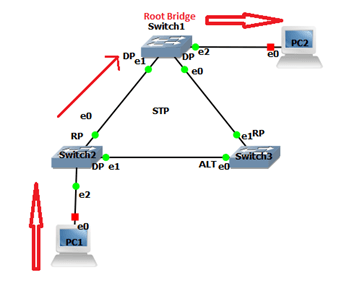
After the attack on the Root Bridge, communication takes place from PC1-SW2-SW3-SW1-PC2.
The attacker connects to SW3 to generate a superior BPDU, which changes port role. ALT port of SW3 changes to RP and takes 30 sec to come to the forwarding state. As the PC1 sends traffic via SW3 after 30 seconds attacker shut down its switch. Re-election of root bridge takes place; this is how the user will be unable to send traffic.
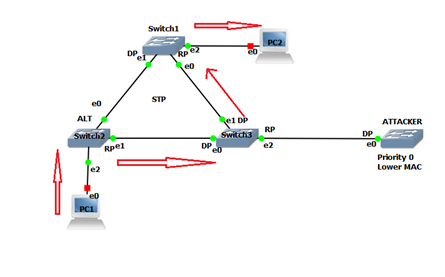
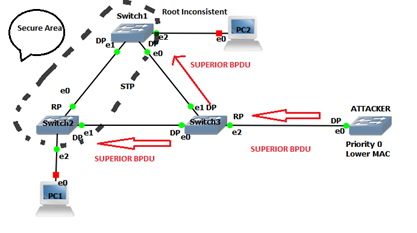
To protect the STP topology from such attack, enable Root Guard on the trunk DP port. Trunk DP port where Root Guard is enabled when receive a superior BPDU goes in the “Root Inconsistent state”. Root Inconsistent state port will be recovered automatically after 20 seconds when attacker remove
Command to enable Root Guard
SW1# interface range e0/0, e0/1
SW1# spanning-tree guard root
Loop Guard
Due to IOS bug SW1 stop sending BPDU. SW3 after 20 second remove the superior BPDU stored at e1 and make it as DP and start sending BPDU received at e0. Alt port e0 is made as RP. There will be no Alt blocking port in the topology. Hence loop occurred.
NOTE- Port where BPDU is not received, BPDU is sent through it. To prevent this loop guard is enabled on RP trunk port.
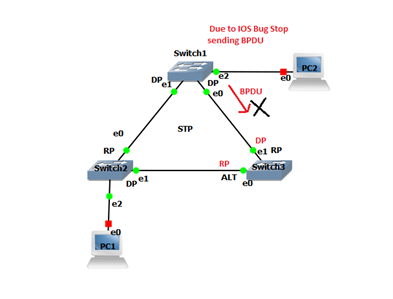
Trunk RP in which loop guard is enabled if try to transmit BPDU will become “Loop Inconsistent State”. As the IOS bug is removed and BPDU is sent from E0 of SW1 and received at RP port Of SW3, it will immediately recover from an inconsistent state.
Loop guard was basically made if fiber optic cable is used between switches. Fiber optic has two wires, one for sending and other for receiving. If one of them is not working still line protocol will be up.
Command to enable Loop Guard
SW3# interface e1
SW3# spanning-tree guard loop
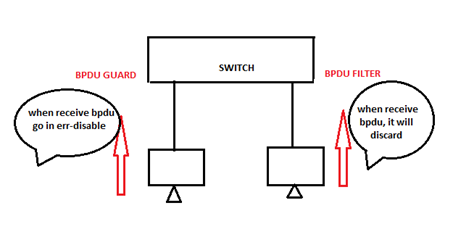
BPDU Guard
In the access port, we will enable BPDU Guard to protect from attackers. Port where BPDU Guard is enabled and when BPDU is sent to it. It will go in an err-disable state, no data plane and control plane traffic are allowed on that port. To recover from err-disabled state manually shut and no shut the interface.
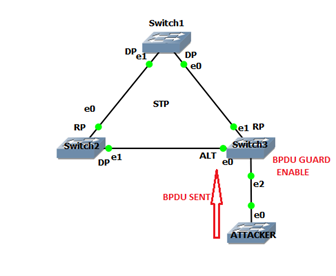
Command to enable BPDU guard
SW2# interface e2
SW2# spanning-tree bpduguard enable
Command to check which interface is in err-disable state
SW# show interface status err-disabled
Command to recover err-disable state automatically
SW# err-disable recovery cause bpduguard
SW# err-disable recovery interval <time>
BPDU Filter
BPDU Filter is applied on the access port. Port, where BPDU Filter is applied, will not send BPDU through it and when received it will simply discard.
Command to enable BPDU Filter
SW# spanning tree portfast default
(All-access ports will be port fast)
SW# spanning tree portfast bpdufilter default
UDLD (Unidirectional Link Detection)
- It is used to detect unidirectional link.
- It is cisco proprietary protocol.
- It is layer 2 protocol.
We enable UDLD on both port of the switch. If the link gets unidirectional, switch will inform.
UDLD has two modes: –
- Normal
In this mode, if the link gets unidirectional, switch will generate log message.
- Aggressive
In this mode, if the link gets unidirectional, switch will generate log message and keep the port in err-disable state.
NOTE: – UDLD can be used for the ethernet cable
Command to enable UDLD
SW# udld enable
SW# interface e0
SW# udld port aggressive
Zindagi Technologies is an IT consulting company having engineers with decades of experience in planning, designing, and implementing Data Centers along with Managed IT Services, cybersecurity, cloud services. If you want to secure your network, we are just a call away. Please ping us on +91-9773973971 or drop us a mail at out and we can get in touch with us.
Author
Jainul Khan
Associate Consultant
