What Do We Understand By Traceroute And How Does It Work?
What is Traceroute?
Traceroute is the tool that network engineers use to troubleshoot the networks, now if we talk about, what does it do?? So, as its name suggests, the main purpose of a traceroute is to trace the path from source to destination, that is how many hops are coming in between the source and destination or tracing the path inside an IP network.
The traceroute commands are available on every host, such as Windows, Linux, macOS and so more, in windows OS ‘tracert’ command is used.
The traceroute will only trace Layer 3 Routers or Hosts, if there is a Wi-Fi access point or Layer 2 switch between two routers, the trace router would be unable to show them even if they are configured with their management IP address to access them.
How does it work?
The traceroute uses the TTL to discover the routes between a source and a destination. In an IP Header, there is a field of 8-bit denoted by Time-to-live (TTL) which goes from 0 to 255. The main objective of TTL is to prevent the packet from being stuck in a loop. So, if there is a loop, since each router decreases the TTL value, at one point it goes to 0 and the packet gets discarded. So, the traceroute uses the TTL value to discover the routers or path between the source and a destination.
Example (for windows): – Here we have one “PC” and three hops (Router) “R1”,” R2”,” R3” that are connected to each other than further connected to the server “S1”.
When we are trying to ping server “S1” we were unable to ping. What could be the reason? The problem can be anywhere between PC-R1, R1-R2, R2-R3, or R3-S1.
If you know the IP addresses of all the routers between the path, we could ping all the routers one by one. But what if we do not know the IP addresses, and how many routers are in between the paths?

When PC (192.168.1.1) tries to send a trace to the S1 (192.168.3.1), then the R1 receives the IP packet and decreases the TTL value to zero and tries to match the destination IP address to itself. Further, it will try to forward the packet to the next router but due to the TTL value being zero the packet will be dropped and R1 sends the TTL Exceeded message to the PC and the PC will print the Next hop in the table.

Again, PC will send the IP packet with TTL value 2 but as soon as R1 receives the packet, it decreased the TTL value from 2 to 1 and forwarded to R2, R2 will again decrease the TTL from 1 to zero and try to forward it to the next-hop but as the TTL value is zero the packet will be dropped and TTL Exceeded message will be forwarded to the PC for R2. Then the PC will print the next-hop on the table.
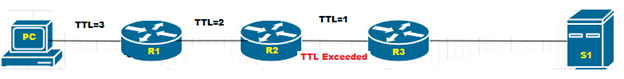
Now, PC will again send the IP packet with TTL value 3, same as the previous scenario the TTL value will be decreased by each router, and the TTL Exceeded message will be sent by R3 to the PC after packet would get dropped.

Now, PC will again send the IP packet with TTL value 4, same as the previous scenario the TTL value will be get decreased by each router, as soon as the packet reached the S1 then The S1 will match the destination IP address by itself and will find self IP address in the IP packet as a destination IP address after the address matched then it will send the ICMP echo reply to the PC, the next-hop will be printed on the traceroute table.
Today we read about how the traceroute command exactly works, This one explanation was only for the windows machine that how exactly traceroute does its job hop by hop and trace the path from source to destination or tracing the path inside the IP Network, further we will continue with the same explanation but on Linux machine in an upcoming blog. Stay tuned for the next part, if you want to see my previously written blogs you can Read them, Meanwhile, for the best Security or Enterprise network consultancy you can contact us on +91 9773973971, Zindagi provides Datacenter services, Enterprise networks deployment, cloud solutions, the establishment of Network infrastructure, cyber security, Cloud Migration which helps your organization to get enhanced over the advanced technologies, we have the experienced team for network security, enterprise network, server virtualization, Datacenter network, ethical hacking and more, you can simply visit our website for more information.
Author
Sameer Vats
Associate Consultant

Irvin Seney
October 8, 2022Having read this I believed it was really enlightening. I appreciate you taking the time and energy to put this article together. I once again find myself personally spending a lot of time both reading and commenting. But so what, it was still worth it!
Judi Bola
February 10, 2023Youre so cool! I dont suppose Ive read anything like this before. So nice to seek out anyone with some authentic thoughts on this subject. realy thanks for beginning this up. this website is one thing that’s needed on the internet, someone with a bit originality. helpful job for bringing one thing new to the web!
popular personal blogs
February 12, 2023Someone necessarily lend a hand to make significantly articles I might state. That is the first time I frequented your web page and thus far? I surprised with the analysis you made to create this actual submit extraordinary. Great task!
look at this web-site
February 17, 2023Hiya, I am really glad I have found this information. Today bloggers publish just about gossips and internet and this is actually annoying. A good site with exciting content, this is what I need. Thank you for keeping this web-site, I’ll be visiting it.
is soundcloud free
February 18, 2023Very nice post. I just stumbled upon your blog and wished to say that I’ve truly enjoyed surfing around your weblog posts. After all I?ll be subscribing for your rss feed and I am hoping you write once more soon!