What is Overlay Network in SD-Access?

In this blog, we are going to discuss SD-Access Overlay Network. You can also refer to it for a basic understanding of SD-Access Wireless.
An overlay network runs over the underlay to create a virtualized network. Virtual networks isolate both data plane and control plane traffic among the virtualized networks from the underlay network. Virtualization is achieved inside the campus fabric by encapsulating user traffic over VXLAN-based IP tunnels that are sourced and terminated at the boundaries of the campus fabric. Overlay networks can run across all or a subset of the underlay network devices.
Campus fabric Overlay consists of 3 important planes:
- Control-Plane based on Locator/ID Separation Protocol (LISP)
- Data- Plane based on Virtual Extensible LAN (VXLAN)
- Policy-Plane based on TrustSec
These concepts are explained in the below section:
Control-Plane based on Locator/ID Separation Protocol (LISP)
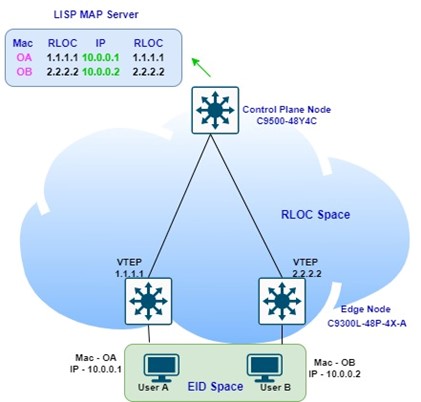
The primary technology used for the fabric control plane is based on the Locator/ID Separation Protocol (LISP). LISP is an IETF standard protocol based on a simple endpoint ID (EID) to routing locator (RLOC) mapping system, to separate the “Identity” (address) from its current “location” (attached router) shown in the below diagram.
A fabric control plane node operates as the database tracking all end-point connectivity to the fabric, and is responsible for the following functions:
- Register all end points connected to the edge nodes, and tracks their location in the fabric (i.e., which edge node the end points are located behind).
- Responds to queries from network devices about the location of end points in the fabric.
- Ensures that when end points move from one location to another, traffic is redirected to the current location.
Data-Plane based on Virtual Extensible LAN (VXLAN)
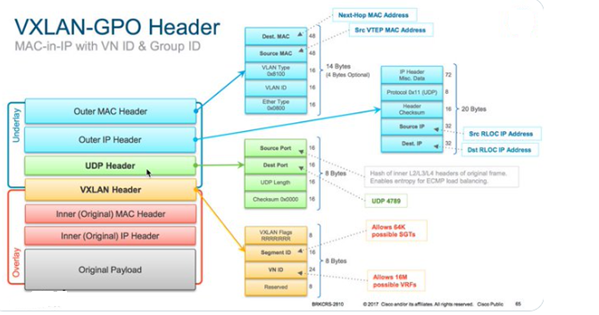
The primary technology used for the fabric data plane is based on Virtual Extensible LAN (VXLAN). VXLAN is an IETF standard encapsulation technology. VXLAN encapsulation is IP/UDP based, meaning that it can be forwarded by any IP-based network (legacy or non-Cisco) and effectively creates the “Overlay” aspect of the SD-Access fabric.
VXLAN encapsulation is used instead of LISP encapsulation for two main reasons:
- VXLAN includes the source Layer 2 header whereas LISP does not.
- VXLAN provides special fields for additional information (such as virtual network [VN] ID and group [segment] ID).
Policy-Plane based on TrustSec
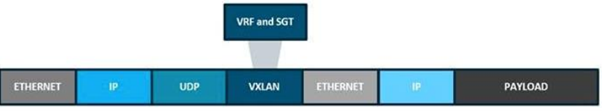
The primary technology used for the fabric policy plane is based on Cisco TrustSec. Cisco TrustSec, and specifically SGT and SGT Exchange Protocol (SXP), is an IETF draft protocol that provides logical group-based policy creation and enforcement by separating the actual endpoint “identity” (group) from its actual network address (IP) using a new ID known as a Scalable [or security] Group Tag (SGT).
This technology provides several advantages for Cisco SD-Access:
- It supports both network-based (VRF/VN) and group-based segmentation (policies)
- It has the ability to create logical policies and dynamic enforcement of group-based policies (regardless of location) for both wired and wireless traffic.
This article explains about SD-Access Overlay Network. We hope that while going through this article, you will be able to understand how Overlay Network works in SD-Access. This SDA Overlay Network provides an optimal traffic flow for the end clients and keeps their identity in MAP Server (Control Plane Node). In continuation of this blog, we will discuss the SD-Access Underlay LAN Automation. You can also refer to another IS-IS blog. You may visit Zindagi’s website or contact us at +91-9773973971.
Author
Sani Singh
Consultant – Enterprise Networking
