What is RADIUS Protocol and its Messages?
RADIUS stands for Remote Authentication Dial In User Service. It is a protocol that is used for network access. All the communication is in clear text except the user password. It earlier uses UDP port number 1645/1646 and now uses port number 1812/1813. It combines authentication and authorization in a single packet and separately for accounting.
What Are The Different Types Of RADIUS Messages?
There are 4 types of RADIUS messages.
- Access-Request
- Access-Challenge
- Access-Reject
- Access-Accept
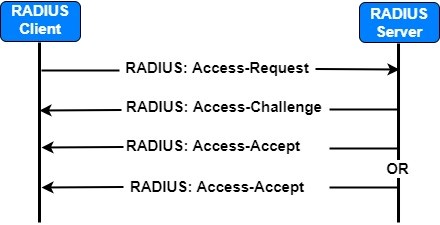
Accept-Request
This is the only Radius message which is sent by the NAD (Network Access Device) to the authentication server. It includes the following:
- Service-type
- nas-port-type
- framed-ip-address
- calling-station-id
- called-station-id
- EAP message
- nas-ip-address
Service-type
It is an attribute of radius which tells the authentication server how the endpoint should be authenticated. For example, username, mac-address
If the service type is:-
- framed – i.e., Dot1x authentication
- call check- i.e., MAB authentication
- Outbound -i.e., Web authentication
nas-port-type
This attribute tells the authentication server how the endpoint is connected, wired connection, or wireless connection.
- Ethernet- wired connection
- Wireless- Wireless
Accept-Challenge
This message is sent by the authentication server to NAD asking for additional information such as passwords. In response, the access request goes from the authenticator to the authentication server. Here authenticator is the NAD device with which the endpoint is connected.
Accept-Reject
If the authentication gets failed, then the authentication server sends the access-reject message.
Accept-Accept
If authentication is done successfully then the authentication server sends the access-accept message.
What Is Dot1x Interface Host Mode?
It means how many endpoints can be authenticated on a single switchport.
There are four dot1x interface host modes.
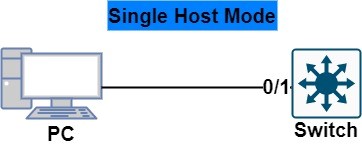
Single Host
One mac address is allowed on an interface. This is the default host mode.
If more than one mac address is learned on the same interface, the switchport will go into an error disable state. Switchport port security is by default enabled on the dot1x interface.
How many VLANs can be configured on a single switchport?
There are two VLANs
- access VLAN Data domain
- voice VLAN Voice domain
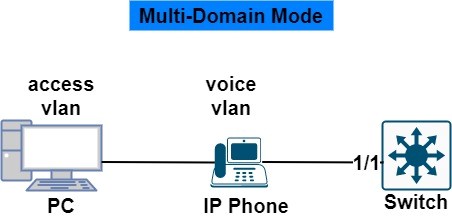
Multi-Domain
One mac address from the voice domain and one mac address from the data domain is allowed.
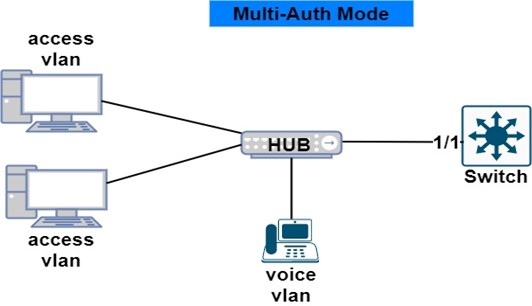
Multi-Auth
One mac address from the voice domain and multiple mac addresses from the data domain. Each mac address must authenticate itself to get network access.
Multi-Host
One mac address from the voice domain and multiple mac addresses from the data domain but only the first mac address from the data domain needs to authenticate. Another mac address connecting later can access the network without authentication.
What Are The Different Types Of Dot1x Deployment Mode?
There are three types of dot1x deployment mode, and it is an approach that needs to be followed when we deploy dot1x in an organization.
- Monitor Mode
- Low-Impact Mode
- Closed Mode
Monitor Mode
In this mode whether a user/mac is authenticated by ISE or not, full access is provided to the user by the switch. The switch will accept any access-accept message from ISE but if ISE sends any access-reject message then the switch will simply ignore that message and provide full access to the user’s failed authentication. Monitor mode is applicable to the wired environment only.
Command on SW# authentication open
Low Impact Mode
In this mode of authentication, an open command is still configured on the switchport but in this, an access list is applied on the switchport manually to limit the traffic for the failed users.
When dot1x is enabled on the switchport only EAP, CDP and LLDP are allowed before authentication.
Closed Mode
This is the actual mode of dot1x and in this, no packet is allowed before authentication except CDP, LLDP, and EAP.
Zindagi Technologies is an IT consulting company having engineers with decades of experience in planning, designing, and implementing Data Centres along with Managed IT Services, cybersecurity, and cloud migration services. If you want to secure your network, we are just a call away. Please ping us at +91-9773973971 or drop a mail.
Author
Jainul Khan
Associate Consultant
Author
