What is Zone-Based Firewall in Networking?
In this blog, we will see how Cisco IOS routers can be used as a firewall by adding Modular Policy Framework (MPF), which is by default enabled in the ASA firewall.
An organization that cannot afford a hardware firewall device can use it as an alternative. These firewall features can be implemented on Cisco IOS routers using stateful firewall functionality with the help of Context-Based Access Control (CBAC) or a Zone-Based Policy Firewall (ZFW) method.
Here we will discuss Zone-Based Policy Firewall (ZFW). A Zone-Based firewall is the successor of CBAC. In a ZFW, a stateful connection is maintained in which source IP address, destination IP address, source port number, destination port number are recorded. The traffic coming from the outside network to the inside network is not allowed, only the replies (of inside the network traffic) whose entry is in the session table coming from the outside network is allowed. To allow outside traffic to reach the inside network, we must make separate zone pairs.
Requirement for Zone-Based Policy Firewall
Zone Creation
Create zones. It is a logical area in which devices having the same trust level reside and an interface is assigned to a zone. Traffic is not allowed between two different zones.
Generally, on the router, firewall functionality is not enabled, we archive this with the help of the MPF.
Modular Policy Framework configuration defines a set of rules for applying firewall features, such as traffic inspection, QoS, etc. to the traffic transiting the firewall.
In creating MPF three main components are-
Class-Map – On the IOS we will use class-map to match the traffic and we can also identify the traffic with the help of Access-List (ACL).
Policy-Map– It specifies what action should take against the traffic identified by the class map.
Service Policy– Specifies where to apply it. The policy is to be applied to an interface or globally.
Zone-pair
Traffic is defined in the class-map and action to be taken (Inspect denied/permit) is defined in policy-map. Then apply these policies to a zone pair, which is always unidirectional and if we want to make bidirectional then we must create another zone pair.
Self-zone
Traffic generated from the router and the traffic destined to the router are known as self-zone traffic. By default, traffic to or from the self-zone is allowed.
How Zone-Based Firewall works-
Zones are defined and named. Can give any name that makes sense, name the zones as inside, outside, and DMZ.
- Inside: Name given to the most trusted (private) network.
- Outside: Untrusted (public) network.
- DMZ: Zone, where we placed servers, inside and outside users, can access these servers.
Security action that will be taken on traffic match in class-map is-
Inspect– Traffic is permitted and inspected and return traffic is also allowed after checking the session table.
Pass– The traffic is permitted and no stateful inspection is done
Drop– The traffic is dropped.
Let us take an example, here we have taken three routers, inside_R1 is in a private network and ZBF_R2 is working as a firewall and outside_R3 is an untrusted public network.
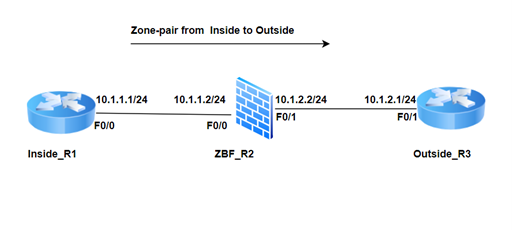
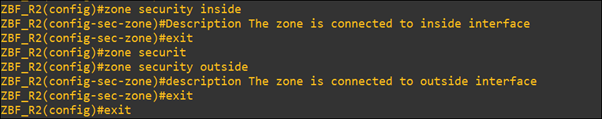
- The First step is to make the reachability between R1-R2-R3. Create the security zone on ZBF_R2.
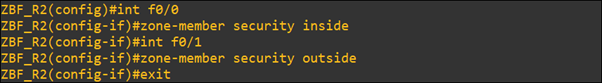
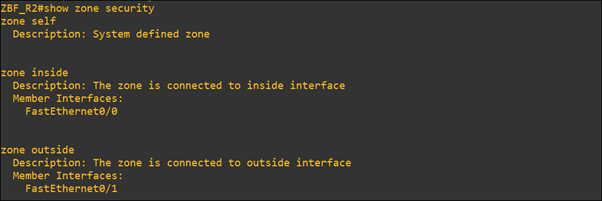
- Assign interfaces to zone
- Define a class map that describes interesting traffic
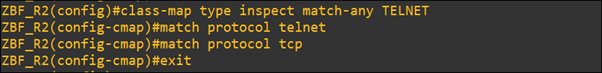
Here we have created the class-map named TELNET and in which telnet and TCP protocols are allowed, the rest of all protocols will match with the default class drop statement.
- Define policy-map to apply action to class-map traffic.
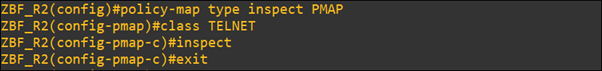
- Apply policy-map to zone-pairs.
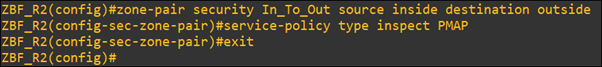
Here zone-pair (In_To_Out) is unidirectional. It allows inside traffic to move outside, and the rest of the traffic is restricted. Traffic from outside is not allowed. To allow outside traffic we must create another zone pair.
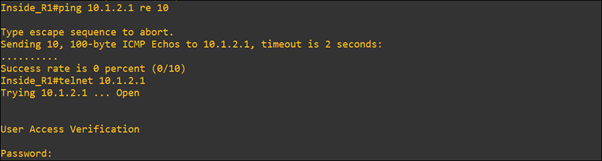
To check traffic match with class-map “TELNET” or default class-map, we will ping inside to outside and after that, we will telnet the outside router (R3_outside) from inside_R1.
As shown below, here telnet match with class-map “TELNET” and ping match in default class-map.
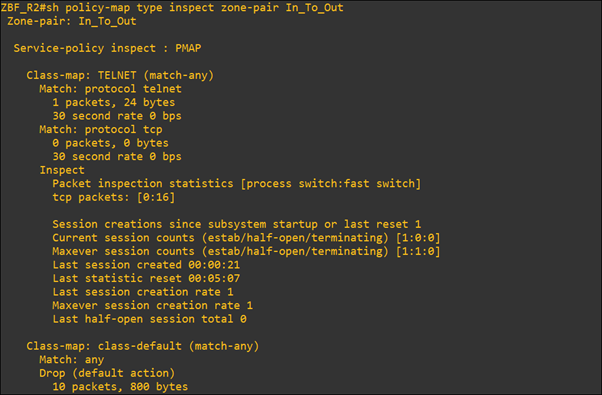
In this blog, we understood how a router can act as a security system with the help of a Zone-Based Firewall (ZBF) feature. We can implement it in a small organization and use the router as the security system also.
Zindagi Technologies consists of experts in the field of Network Security, Data Centre technologies, Enterprise & Service Provider Networks, Virtualization, Private Cloud, Public Cloud, Data Center Networks (LAN and SAN), Collaboration, Wireless, Surveillance, ACI, storage, and security technologies. With our help, you can take your business mile-mile ahead. To know more about us, visit Zindagi or call us on +91-9773973971.
Author
Prakash Raghav
Senior Consultant Enterprise Networking

lasixboamE
December 6, 2022I’m not sure where you’re getting your info, but good topic. I needs to spend some time learning much more or understanding more.
Thanks for wonderful information I was looking for this info for my mission.