How to do Steganography and what are its types?
The agenda of this blog is to try to understand Steganography Basics, its diverse types, and some tools so that you can do the hands-on practice.
What is Steganography?
- It is a practice of hiding messages in plain sight. It is a Greek word that means Stegano → “covered” & Graphia → “writing”.
- It is not a new or 21st Century Technique but it is an incredibly old way to pass some Important messages like
- Shaving the head of Messenger and tattooing the clean shaved head of Messenger and finally waiting for the hair to hide the message.
- Usage of Invisible INK.
Steganography VS Cryptology or Encryption?
- We can say Steganography is “Sister-Science” of Cryptology
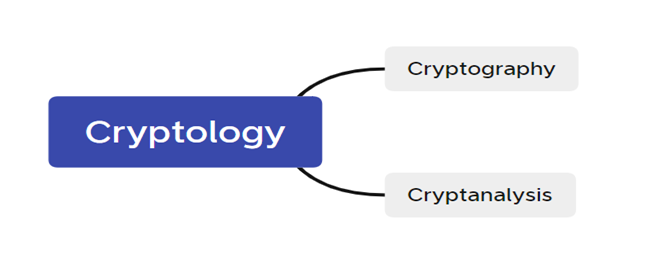
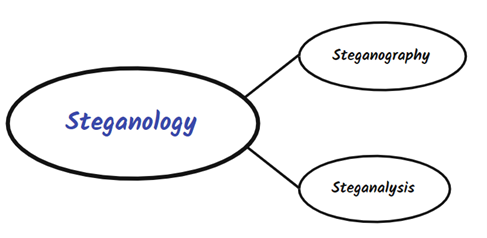
- In Cryptology we know that there is a message, but we cannot read it since it is encrypted, and we need a Cryptoanalysis.
- In Steganography we don’t know that there is a Message while the encryption part is optional
Now with a basic understanding of Steganography, it is time to understand its classification and how we can do it.
Types of Steganography
In the modern World i.e., the 21st Century we have different Digital Mediums to hide the messages like Image Files, Text / Document Files, Video Files, Music Files, and based on these several types of Files we can Classify Steganography.
- Text Steganography
- Image Steganography
- Audio Steganography
- Video Steganography
Text Steganography: Using Cryptool
Text Steganography means hiding messages in a Text File and we can do that in different ways by using CRYPTOOL.
- Capital Letters
- Capital Letters [ Binary Code]
- Letter Marking
- Letter Marking [Binary Code]
- “Zero with Spaces”
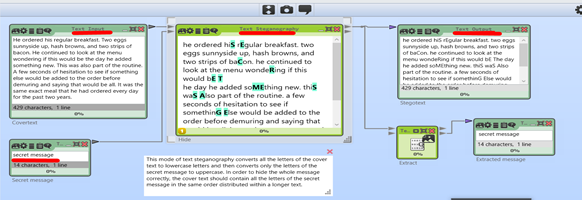
Capital Letters:
In this mode, we convert all the letters of the Cover Text to lowercase and then convert only the letters of the Secret Message in Uppercase. From the Below Image, you can see how CRYPTOOL hides our Secret Message.
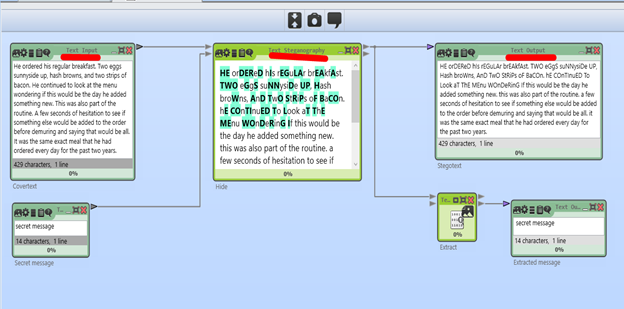
Capital Letter [ AS Binary Code]:
This mode of text steganography converts the secret message to bits and converts the letters in the cover text to uppercase when the bit is 1 at the same index in the bitstring or leaves the letter in lowercase when the bit is 0 at that index. Therefore, to hide all of the messages correctly, the number of letters in the cover text should be equal to or greater than the number of bits in the secret message.
In the below example,
The secret message starts with “se”, which in ASCII is 0x73 and 0x65 and in the binary form it is “01110011” and “01100101”.
Then the binary sequence of each secret character is reversed, so we get the bitstream: “11 00 11 10 10 10 01 10”.
The conversions for the first 16 (nonblank) cover-text letters then look like this: He ordered his regu [original cover text] he ordered his regu [cover text in lowercase] HE ordered hIs rEGu [cover text adapted according to the bitstream] 11 0011101 010 0110 [bitstream used for adapting the case of the letters]
CRYPTOOL offers numerous ways to do TEXT Steganography.
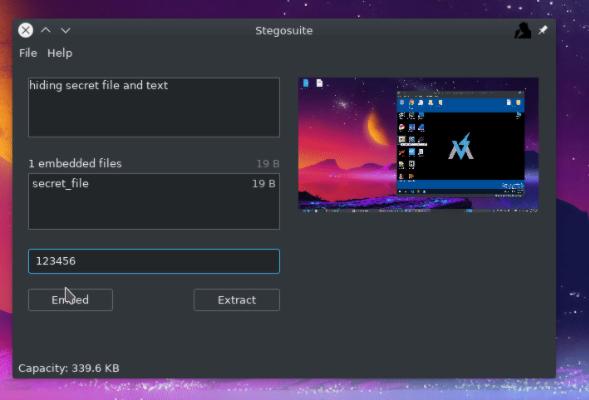
IMAGE Steganography: Using Stegosuite
In this type, we hide Data by replacing some Pixels of an Image with our Secret Message.
Using Stego-Suite it’s remarkably simple. The below Images show how to use this tool we can Hide a Text Message as well as File in an Image File.
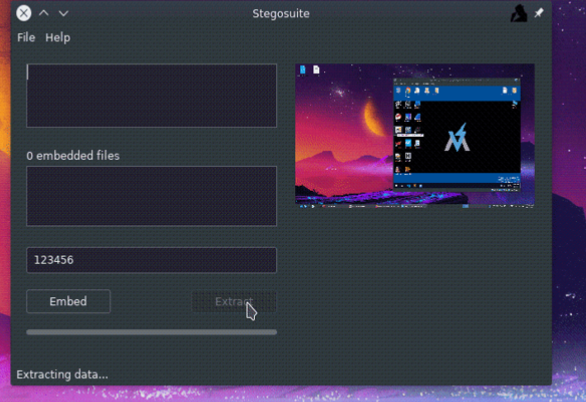
Using the same tool we can Reverse the Process, that is, we can Extract the secret Message if it is present from an Image.
AUDIO Steganography
We can do Audio Steganography in two ways:
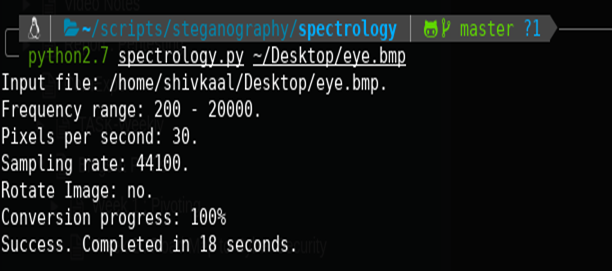
- Directly converts the Secret File into its Audio Form —->>> spectrology.py
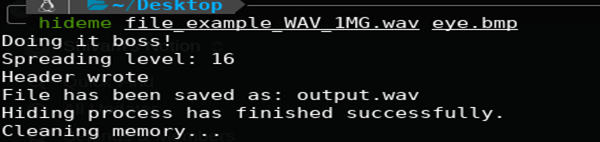
- Hide the Secret File into an Audio File —>>> AudioStego
To Visualize the Audio Spectrogram, we use Sonic Visualizer.
Hiding data Using Spectrology.py
So, this is our Secret File which we hide in an Audio File
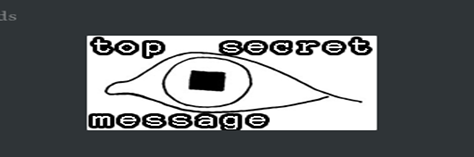
Now using the following command, we can convert this Image file into an Audio File.
Hiding Data using AudioStego
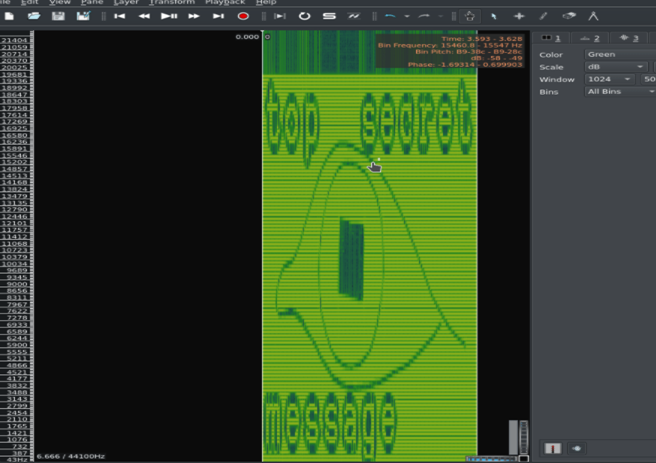
Analysis of Audio File using SONIC
And if we do an Analysis of that Audio File using Sonic
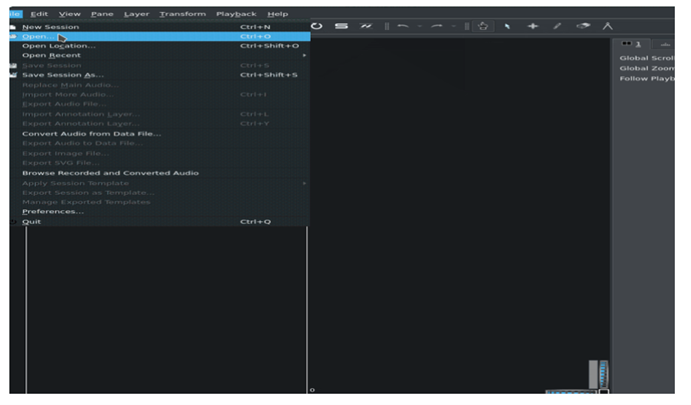
Step 1: Open Audio File

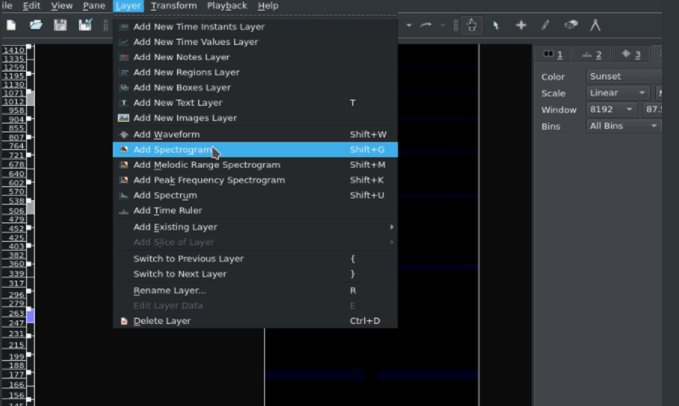
Step 2: Go to Layer-> Add Steganograph
Video Steganography: Using OpenPuff
Video Steganography is another type in which we hide our Secret File into a Video File.
Using OpenPuff we can hide & unhide the Secret File and it is quite simple to use.
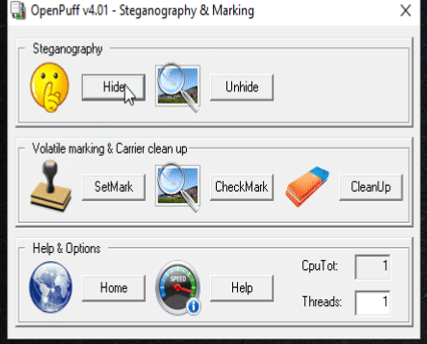
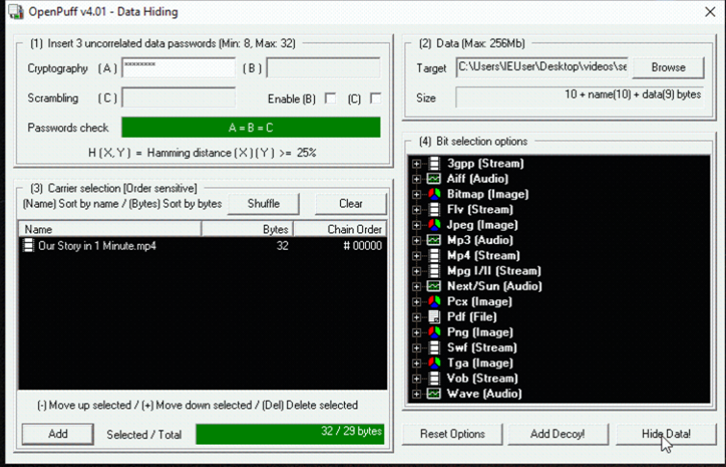
Hiding of Secret File.
Step 1: Click on HIDE Button
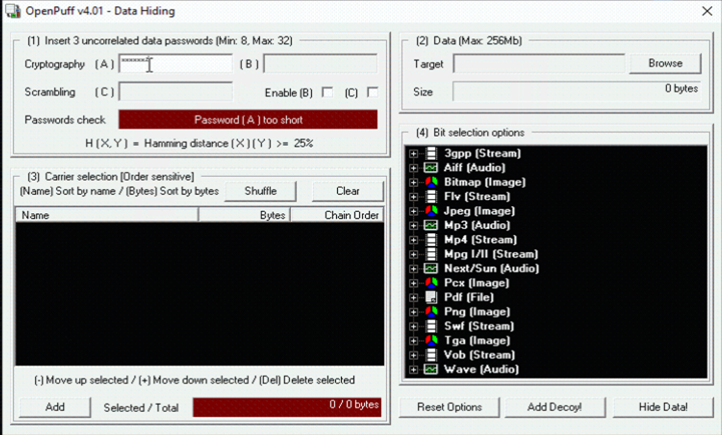
Step 2: Add Password in Cryptography
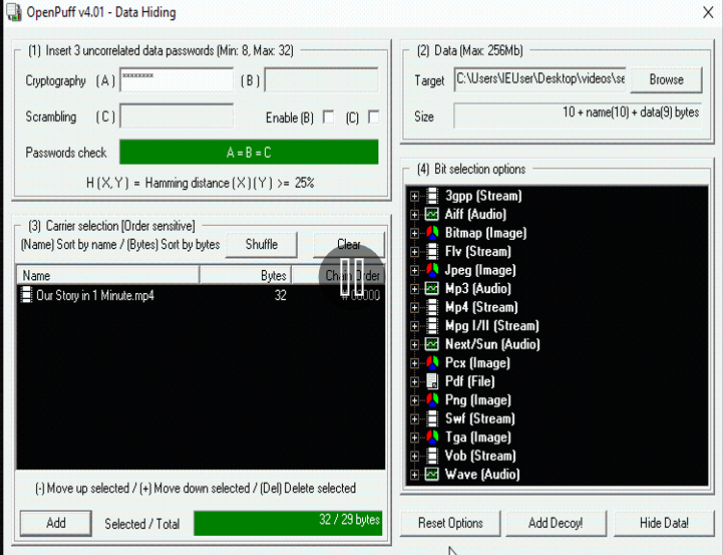
Step 3: Add Secret File in TARGET Field and Video File by clicking on ADD Button
Step 4: Click on HIDE DATA Button
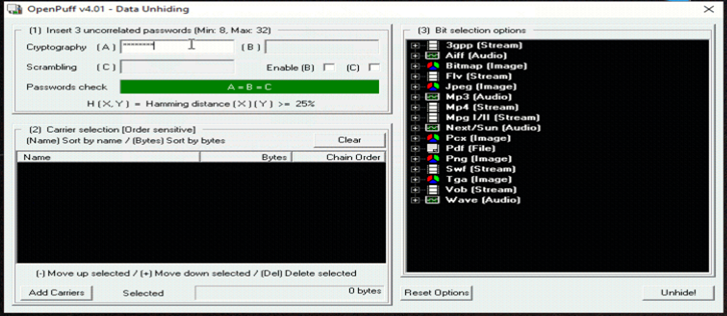
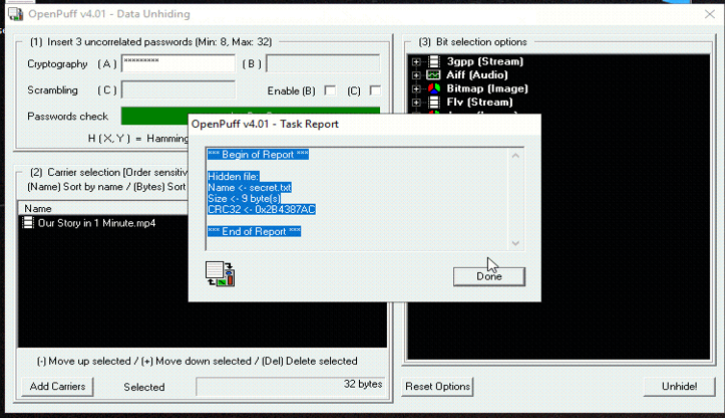
Unhiding of Secret File
Step 1: Click on UNHIDE Button
Step 2: Add Password in Cryptography
Step 3: Browse Video File which contains Secret DATA by clicking on Carrier Button
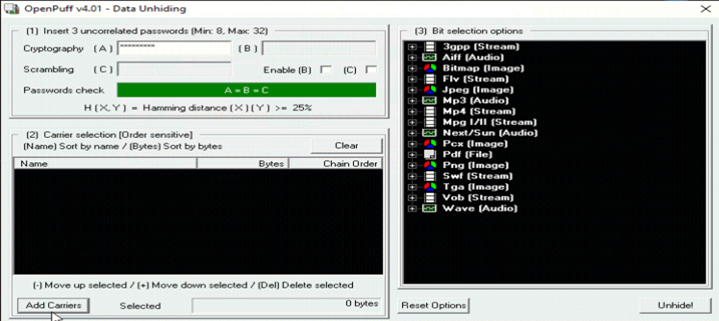
Step 4: Click on Unhide Button
Well, there is one more way we can do Steganography but that is Out-of-scope from this blog, and we don’t have many Sophisticated Tools to do that.
Network Steganography:
In this type, we hide our Secret Message / File in the Headers Section of various Network Packets. We select those Headers which are not in use in Normal Communication.
Using Steganography and Encryption an Abuser can send malicious data in an Enterprise Network which can harm the users as well as your precious data to overcome such types of Cyber-Security Challenges a Security Component like a Firewall helps you to protect your Network
Our team at Zindagi Technologies consists of experts in the field of Data Centre, Virtualization & Cloud Services, Collaboration, Wireless device Deployments, and many more technologies that will provide you with our services and we will be glad to provide you with our Services, give us a call at +919773973971.
Author
Shivam Choudhary
Associate Consultant
