The working of Policy Based Routing (PBR) with Internet Protocol Service Level Agreement (IP SLA).
In this article, we are going to discuss how Policy Based Routing (PBR) works with IP SLA. Apart from this blog, I have written other technology blogs that you can read when you click here.
What is PBR?
PBR stands for Policy Based Routing. It is used to overrule the routing table. The overrule means, we can manipulate the path on the basis of source IP.
Usually, we manipulate the path on a destination based. In the below diagram, we can see that R1 receives the prefix 40.0.0.0/24 via R2 & R3. Let’s suppose, we are using the EIGRP routing protocol. Hence, R1 will update the prefix 40.0.0.0/24 into its routing table via R2 as the cost link between R1 & R2 is 1.
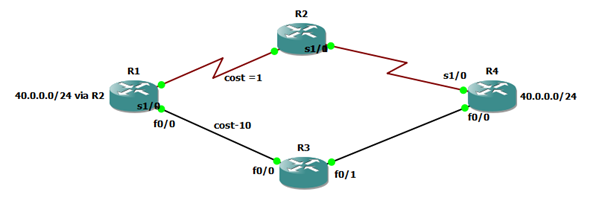
What if we want to update the prefix via R3? For that, we can use the offset value and increase the link cost between R1 & R2 or we can advertise the summary route from R4 to R2. Thus, the router R1 will update the prefix via R3. These are destination-based path manipulation.
But with the help of PBR, we can manipulate the path on a source based.
How to apply Policy Based Routing?
In the below diagram, we can see that the user with IP address 10.0.0.10 will communicate to prefix 40.0.0.0/24 via R2 as per the routing table decision.
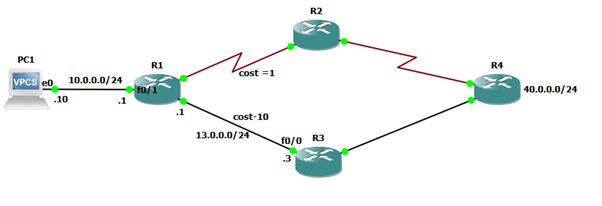
But we can manipulate the path via R3 by creating and applying PBR.
We will create a policy that tells the router that whenever a user comes with a source IP address 10.0.0.10 and destination IP address of any prefix 40.0.0.0/24, it must pass via the next hop IP 13.0.0.3. And, we will apply that policy on the ingress port of R1, so that it will not check the routing table, and just on the basis of its PBR policy, it will forward the packet towards 10.0.0.3.
Here, we can see the path manipulation without any changes in the routing table. That is why it is called Source based path manipulation.
Steps for Configuring Policy Based Routing.
The following are the steps for implementing PBR:
- Define Interesting Traffic: We can use extended ACL to define the interesting traffic.
Syntax: access-list <number> permit ip <source ip> <destination network id> <wild card mask>
For example:
(Config-t) # access-list 101 permit ip 10.0.0.10 40.0.0.0 0.0.0.255
- Route–Map: We will create a route map and match the interesting traffic with the route map.
Syntax: route-map <name> permit
Match ip address <access-list number>
Set ip address <next-hop ip>
For example:
(Config-t)# route-map CCNP permit
#match ip address 101
#set ip next-hop 13.1.1.3
- Call on Interface: We will call the route map on the ingress port.
Syntax: interface <port id>
Ip policy route-map <route map name>
For Example:
(Config-t)# interface f0/1
# ip policy route-map CCNP
Zindagi Technologies has proven its expertise for years in providing Campus LAN technology solutions in various enterprise and corporate networks in which PBR is one of the examples that help to manipulate source-based paths. Zindagi Technologies have all its doors open to receive queries related to Cyber Security challenges, and cloud computing requirements and we will be glad to support you. Being the top IT consulting company in Delhi, we are ready to help you in securing your data and give an IT consultation that will work best for you. Get in touch with us and let’s get your data secured call us at +91-9773973971.
Author
Sani Singh
Consultant – Enterprise Networking
