What Is Data Center Security And Why It Should Be Implemented?

When an organization keeps a Data Center as the data storage unit then it is important to keep up with the security of the data center. To keep the operations, applications, and data safe from threats, data center security is implemented as it is the physical and digital support system. For this, you can avail yourself of Hybrid Data Center services in Delhi. When we talk about data centers then we are talking about shared access to critical applications, complex networks, storage, and compute infrastructure. The industry standards are such that they assist in the data center design, maintenance, and construction. This ensures that the data is secure and does not have any availability issues.
Providing Physical Data Center Security
There are many physical threats by which the data centers have to be protected. A secured location, physical access controls of the buildings, and the monitoring systems that keep the data center facility secure. It’s not just the data center security, but the IT infrastructure requires a comprehensive Zero trust analysis integrated into any data center design. It is very important to understand the security measures as companies migrate the on-premises IT systems to the cloud.
Securing The Location

Hybrid Data Center services in Delhi will give you multiple choices where you can build your Data Center.
- The location in which the data centers are to be placed should be secured
- An area that is not prone to earthquakes, fires, or floods. Although it is impossible, the area selected should be least prone to these calamities.
- A façade is free from company logos and disguised.
- Barriers to prevent any sort of forced entry
- Limit the entry points.
Controls That Can Be Accessed Physically
Defense-in-depth strategies are used in data center security best practices for physical access restrictions. Setting up multiple layers of access controls and requiring access to each layer is one such defense. Multiple layering means the entry might be by the help of biometrics and then the next step would be physical verification by security personnel. The zones would be different in the data center and access would be required for each zone including all the surveillance monitors in the area.
Securing Building Management Systems
One has to secure every point of access in the data center and these includes:
- Secure access from all remote technicians who oversee maintaining MFA. Only access should be given is enough for their job. You should also ensure that the device is secure before you grant access.
- The buildings including HVAC, elevators, IoT device, and similar solutions systems has to be secured also.
- Separating Wi-Fi networks and building systems from production networks to stop lateral movement.
- Continually checking the network for the presence of unfamiliar or new wireless access points or IoT devices.
IT Security Access Controls Of Data Center
The following security protocols are to ensure the main goal of data security which is securing the servers.
- Enabling those services which are needed
- Allowing access to the services depending on the business needs
- Latest security patches updated systems.
- Using secure protocols such as SSH and HTTPS.
- Gaining power control over firewalls for increasing network security
- Macro segmenting north/south traffic by using firewalls at boundary points.
- When necessary, encrypt communications in transit.
The security should not be a bottleneck and to ensure this, the data center security solutions should follow:
- Support security at network speeds of 10, 25, 40, and 100 Gbps and higher.
- Meet the capacity needs of the data center.
- Scale when networks experience seasonal traffic spikes from e-commerce web servers, for example, or from hyper-scale security.
- Create backup systems that can be updated without affecting the functioning of the data center.
Using The Correct Security Tool For The Job

As we know that different systems are protected by different security solutions and one such example we can give is that the perimeter-focused security solutions are designed to provide protection to the clients and the servers are protected by data center security solutions. The enterprise network clients, having all the access to the internet needs protection that prevents threats in email and the internet. Application control also has to prevent the use of risky applications. The protections include:
- Anti-phishing
- Anti-ransomware
- Remote browsing isolation
- Sandboxing
- Content Disarm and reconstruction.
- Forensics
The data centers are made of servers and not user devices so these security measures do not apply to them, but the following security measures apply to the data centers:
Intrusion prevention system – It identifies and stops network-based attacks on weak systems. IPS may be used as a virtual patching solution to prevent exploits until fixes can be installed when systems cannot be patched.
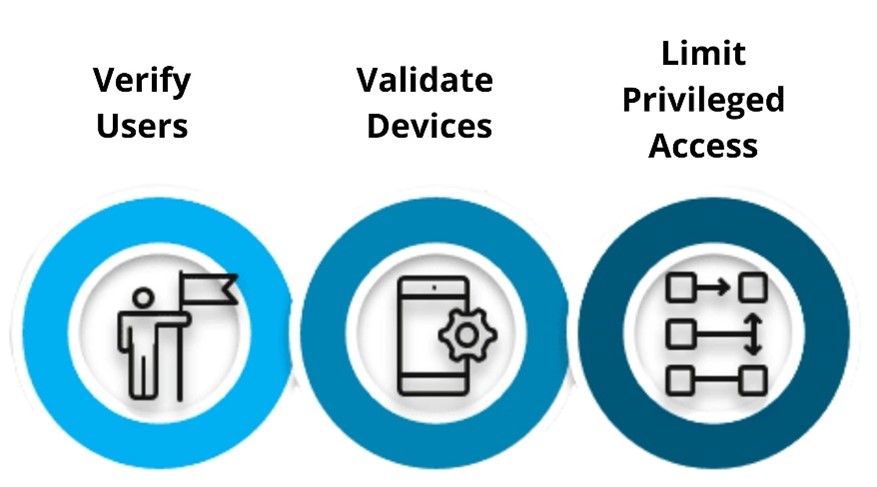
Zero-trust Network Access – Also known as Software Defined Perimeter – is a safe way to connect users, regardless of their devices or location, to any business application.
Web security – Web application firewall and web application and API protection (WAAP), its contemporary cloud part, is installed on the network edge and scrutinizes traffic to and from web applications.
Employ Security Measures That Support Data Center To Cloud Migration.
Companies now spend roughly the same amount on cloud infrastructures as they do on infrastructures for on-site data centers. It’s crucial to retain the same security when businesses shift their IT assets to the cloud. In order to do this, security must connect with data center networking innovations like VXLAN and software-defined networking, support virtual environments and cloud-native APIs, and Software-defined Network (SDN). Zindagi Technologies is a provider of Top Hybrid Data Center Services in Delhi and have catered to many public and private sectors in design, deployment, and implementation. Give us a call at +91 9773973971 or drop an email and we will get in touch with you with a Data Center security plan.
Author
Shweta
Senior Executive, S&M

Increase Agility by Extending IT Teams With Managed IT Services | Zindagi Technologies
August 4, 2022[…] today is data center upgradation, then tomorrow it might be migration to the cloud or security upgradation or deploying […]
Use of VX-LAN in Data Center | Zindagi Technologies
September 8, 2022[…] How does VX-LAN work in DATA CENTER? […]