What is the Importance of Threat Grid and what are the Different Types of Interfaces
In this blog, we will see the importance of Threat Grid and what are the different types of interfaces in this appliance. Threat Grid (TG) is a Sandbox appliance that is very important for the network.
Importance of Threat Grid (TG)
A Cisco Threat Grid appliance provides safe and highly secure on-premises advanced malware analysis, with deep threat analytics and content. Threat Grid Appliances provide the complete malware analysis platform.
The appliance allows organizations to submit malware samples that are subject to various compliance and policy restrictions.
Many organizations deal with sensitive data, including banks, health care providers, etc., that must follow various regulatory rules and guidelines that will not allow certain types of files, such as malware to be sent outside of the network for malware analysis.
By maintaining a Cisco Threat Grid Appliance on-premises, organizations can send suspicious documents and files to it to be analyzed without leaving the network.
Security teams can use a Threat Grid Appliance to analyze all samples using highly secure static and dynamic analysis techniques.
Analysis results are correlated with hundreds of millions of previously analyzed malware samples, to provide a global view of malware attacks and campaigns, and their distributions. Observations of one sample of activity and characteristics can quickly be compared against millions of other samples to understand its behavior in a historical and global context. Advanced malware attacks and threats can be effectively defended through this capability.
Different Types of the Interfaces in Threat Grid (TG)
We have 4 types of interfaces in TG which are as follows:
- Admin Interface
- CIMC Interface
- Clean Interface
- Dirty Interface
We will see one by one about the above-mentioned interfaces and their uses.
Let’s take an example of the Topology with all the interfaces, so we can understand this very easily.
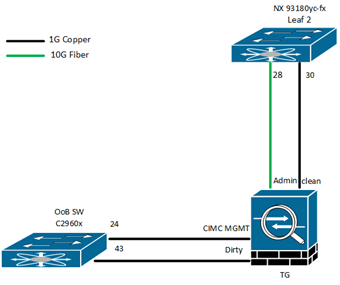
In the above diagram, I have my TG deployed, which is connected with 2 switches. The 1st switch is the OOB (Out of Band) Switch for its CIMC management and Dirty interface and 2nd Switch is Nexus Switch for TG Administrator Access and Clean Interface.
I used 2 types of links, 1G copper for CIMC, Clean and Dirty Interfaces, and 10G link for Admin Interface. Types of Interfaces/links totally depend on the model and hardware of the appliance. For a better understanding of the hardware, you can check the datasheets of the Cisco.
You can also check the features and benefits, Supported Platforms, and Licensing of the appliance.
- Admin Interface
This is the main Threat Grid user interface for configuring the appliance. In addition to licensing, email host, and SSL certificates, most Threat Grid Appliance configuration options are available through the Admin UI.
- CIMC Interface
When Cisco Integrated Management Controller (CIMC) interface is configured, it can be used to manage and maintain servers.
Note – The CIMC is not supported on the Threat Grid (TG) M5 Appliance server.
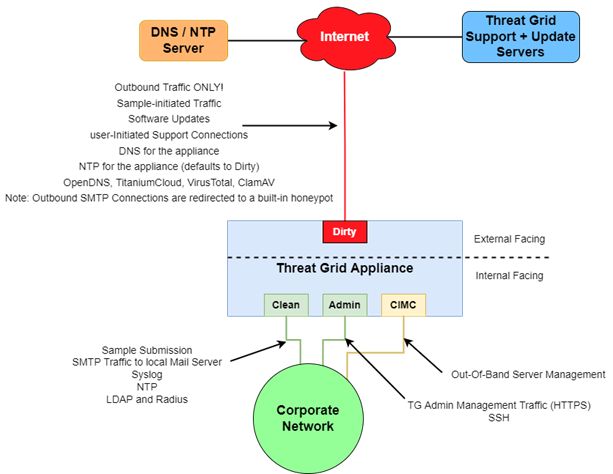
- Clean Interface
It is still essential that Clean is accessed through corporate networks, but no outbound communications towards the internet are required. We use this interface for ‘Sample File submission’.
The other uses of this interface are:
- API and UI traffic – (inbound)
- Simple Mail Transfer Protocol (SMTP) – (outbound connection to the configured mail server)
- SSH – (inbound for TGSH Dialog)
- Syslog – (outbound to a configured Syslog Server)
- WSA, ESA, and CSA Integrations
- AMP – (for Endpoints Private Cloud Integration)
- DNS – (optional)
- LDAP – (outbound)
- RADIUS – (outbound)
- NTP – (for using an internal NTP server)
- Dirty Interface
This interface requires Internet access and uses for outbound connections only. Your own DNS (private IP) should not be used for the Dirty Interface, as traffic sent to a private IP will be blocked by the Network Exit Localization firewall.
The other uses of this port are:
- NTP (defaults to Dirty)
- Updates
- Support session in Normal operations mode
- Support snapshots
- Malware sample-initiated traffic
- Recovery mode support session (outbound)
- OpenDNS, TitaniumCloud, VirusTotal, ClamAV
- SMTP outbound connections are redirected to a built-in honeypot
I hope this blog will be helpful for you to understand the importance and types of interfaces of Threat Grid. The mentioned deployment topology in this blog is not mandatory, you can use it as per your requirement, but the allowed traffic of the interfaces is mandatory.
You can also check my latest blogs on multiple technologies. The key to success is information and Configuration. Blogs of Zindagi Technologies will give you both.
Zindagi Technologies is an IT consulting company that has proven experience in cybersecurity, cloud security, Network Security, managed IT, and other services also. You can easily contact us or call us at +91-9773973971.
Author
Jagjeet Singh
Senior Network Security Consultant
