How to Implement 802.1x on your wired network?
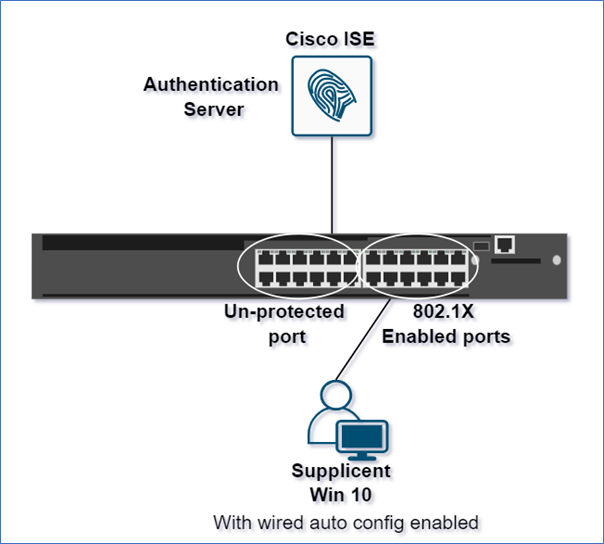
Regardless of the fact that next-generation LANs should indeed be built on SD-Access technology, many businesses currently use an intermediate solution to secure their wired networks. This entails using a mix of 802.1x and MAC Authentication Bypass (MAB). The endpoints that connect to the access layer can be authenticated and authorized using those techniques. Many other blogs concentrate on configuring access switches or the Cisco Identity Services Engine (ISE). Instead, we would want to describe how we approach engineering and what you should think about.
Many fully skilled engineers are familiar with all ISE features and can explain packet-level specifics for various flows. They frequently focus on explaining complex features while neglecting to consider the larger picture. Increasing network security across many switches in a brief period is frequently the aim. It’s possible to improve it more, but it is not practical to go from no 802.1x or MAB to the most complicated deployment immediately.
Before implementing wired 802.1x, plan and design
An organized strategy for planning, designing, and implementing the solution is frequently absent. Every project should always begin with a network assessment to determine the present arrangement. The network design, where you may show the concepts to the customer, should come after this initial essential step. Do not be tempted to skip those phases and go right to solution implementation; it will cost you money eventually. Lack of preparation will never save time but will instead result in delays and unplanned outages.
The blog will enable you in seeing multiple problems on paper rather than during the change window. It will assist you in providing a solution that is flexible enough to allow for the addition of more complicated features in the future. Nobody enjoys undoing a modification or having to re-implement a significant proportion of a solution. Before making any modifications, you must first complete this extensive preparation. Finally, excellent documentation will serve as a solid platform for training and project handover. Accept it because it will save you a lot of trouble.
802.1X Monitor, Low Impact & Secure Mode, or Closed mode
There are several publications on the Internet that discuss the three basic stages of wired 802.1x deployment. These are the phases:
Monitor Mode
Set up your access switches with MAB and 802.1x but disregard the RADIUS (ISE) answer and enable connectivity regardless of the authentication outcome.
- Even failed authentication will allow access.
- Network admin can: – See who would have failed, no effect on user and endpoint access, AAA Radius accounting provides visibility into 802.1x operation.
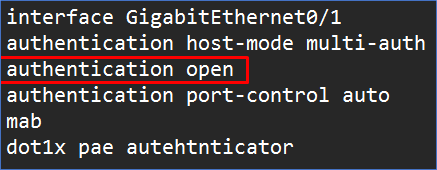
Low Impact Mode
Allows simply basic DNS, DHCP, and AD communication, but any additional connectivity requires successful ISE authentication.
- Limited basic access prior to the authentication
- Port ACL applied to switch interface
- Grant specific access after successful authentication
- DACL received from server (ISE Server)
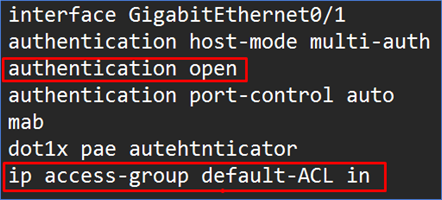
Secure Mode
Only accept EAPoL and prohibit all other communication from the endpoint until it is successfully authenticated in Secure Mode also known as Closed mode.
- Most restrictive mode
- No access prior to login (Only EAPoL allowed before)
- Specific access after successful authentication
- Default 802.1X behavior
- No auth open, no ACL, which means they are referred to closed mode.

When you configure the switch in Monitor Mode, you will need to add the command “authentication open” to each port. The only difference between Low Impact and Secure Mode is the presence of an access list on the interface, which is necessary to allow MAB-authenticated devices. When ISE becomes inaccessible while an ACL is in effect, using Low Impact mode might cause issues. When ISE is unavailable, customized EEM scripts would be required to remove the ACL and allow a vital VLAN. What is the justification for implementing wired authentication in such a staged manner? Is it always necessary to set up all switches at least twice to accomplish the same goal?
Start The Wired 802.1x Implementation On A Group Of Switches
You must begin the discovery process on a slightly smaller scale to design your ISE policy for wired endpoints. It is preferable to choose a few switches that are indicative of the entire estate. The method for choosing those switches might be different, but it should involve the following:
- Different switch models
- Different types of endpoints linked to the switches
- If applicable, software versions
You will obtain a lot of information about the devices linked to your network after you begin your implementation on those switches. This Proof of Concept will allow you to test the solution on a smaller scale to ensure everything is working properly. You will also find any potential software flaws, which can help you choose the optimum software version for a big deployment. You should have a lot better concept of how you need to build your future policies at the end of this POC phase. It’s quite possible that you’ll have many configuration templates, some of which may offer multi-domain or multi-auth choices.
Using Wired Authentication On Your LAN Is An Excellent Way To Get Started With SD-Access
Identifying the endpoints connected to their LAN would be an issue for many enterprises wanting to adopt SD-Access. The typically wired authentication discussed here, and SD-Access have significant basic differences in policy enforcement. Based on the ISE authentication result, the access switch in conventional networking enables, refuses, or restricts access for each endpoint. It works differently in Software Defined Access since ISE generates Scalable Group Tags (SGTs) based on the authentication result. These SGTs implement a data plane policy based on a connectivity matrix established on ISE and transmitted to the edge nodes. In order to offer the right SGT in any SD-Access architecture, you must first verify your endpoints. Starting reconnaissance and deploying conventional wired authentication on your LAN now will get you one step closer to realizing your SDA goal in the future.
We here at Zindagi Technologies, have a team of certified Subject Matter Experts who specializes in SD-Access solutions. If you are looking for Planning / Designing / Implementation / PoC services for SD-Access, reach us out at Zindagi Technologies Pvt. Ltd. Or drop us a WhatsApp at +91-9773973971.
Author
Ravi Kumar Singh
Consultant – Network Security
