What Is Man In The Middle Attack (MITM) And What Are Its Types? (1)
When two people are sharing information or just talking with each other but suddenly a third person comes and stands between the two, silently hearing the conversation. Then he uses the information against them, creating misunderstandings and problems. This is exactly Man in the middle situation.
In our previous blog, we learned about the prevention of password attacks whereas, in this blog, we will learn about the Man in the middle attack and the types of attacks that fall under it as it is one of the password attacks.
How Are The MITM Attacks Carried Out?
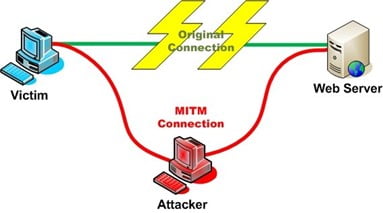
When a hacker or attacker places in between the exchange of information between the two trusted parties, stealing the data and tampering with it.
One of the major examples is when the attacker intercepts the communication and talks with each other. Both of them think that they have been talking to the concerned parties but in reality, they both have been talking to the attacker. In another case, the browser is compromised by the attacker with the help of malware or virus. Once the browser handle is in the hands of the hacker, he/she can send any information to any source without a barrier. They can have your login credentials, passwords, saved data, bank acc number, and a lot of other types of sensitive data.
There are 7 types of Man In The Middle attacks and in this blog, we will discuss 3 types first. The rest 4 types will be discussed in the next blog.
DNS Spoofing
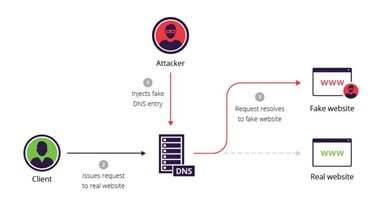
This is a type of spoofing that creates a replica of the server and directs the requests on that instead of the real server. Suppose you have to login to your bank website say www.merabank.com. While the victim is logging in, the hacker will intercept the request and will return the IP of the malicious server instead of the real server. The malicious server looks similar to the real server but it’s not and as soon as the person logs in with the id and password, the information will be sent to the hacker’s server.
HTTPS Spoofing
HTTPS cant is spoofed but this does not mean that you are safe. Hackers create domains that are similar to the website you are visiting. Hackers register a domain name that is similar to the original website with minor changes that are barely noticeable. Even the SSL certificate is registered to make it look original. Since most people don’t read the URL and end up clicking the wrong address. The user thinks that it is a legitimate site and fills in all the details that the hacker has asked. At one time, Apple Inc spoofed website was also ready, and the data was stolen by the hacker.
Man In The Browser (MITB)
This type of MITM attack is used to carry financial fraud. This is similar to the MITM attack but in this case, the hacker inserts himself in the communication of two people in order to eavesdrop so that he can hear the sensitive information. Most of the time Trojan Horse malware is used to carry out the attack.
In the next blog, we will briefly explain the 5 MITM attacks; SSL Stripping, Email Hijacking, Wi-Fi Eavesdropping, and Session Hacking. Stay Tuned. Call us on +91 9773973971.
Author
Shweta
Senior Content Writer
